Complete Visibility with Real-Time Monitoring!
Manage applications, servers, and logs from a single, unified platform.
Complete Visibility with Real-Time Monitoring
Manage applications, servers, and logs from a single, unified platform.

-
 Proactive Monitoring
Proactive Monitoring
Proactive Issue Resolution
• Proactively identify and resolve issues.
• Real-time monitoring of key metrics.
• Prevent user impact.
-
 Unified Monitoring
Unified Monitoring
Unified Infrastructure View
• Centralized overview of applications, servers, and logs.
• Eliminating the need for multiple tools.
• Significantly reducing the Meantime to Resolution (MTTR).
-
 Workflow Automation
Workflow Automation
Streamlined Workflows
• Reduce manual tasks.
• Improve IT efficiency.
• Automated alerts and notifications.
-
 Security Monitoring
Security Monitoring
Enhanced Security
• Monitor for any suspicious activity.
• Immediate alerts for potential threats.
Why Choose Lert?

Real-time monitoring
Gain instant insights into application performance, server health, and resource utilization.

Comprehensive log management
Centralize and analyze logs from various sources for faster troubleshooting and root cause analysis.
Reporting and analytics
Generate detailed reports and gain historical insights to identify trends and optimize your infrastructure.

Integrations
Connect with various third-party tools and services to enhance functionality and automate workflows.

Customizable dashboards
Create personalized dashboards with relevant metrics and visuals for efficient monitoring.

Advanced alerting
Set up custom notification rules to receive alerts via email, SMS, or other channels based on specific events.
Solutions for Every Business Need
Application performance management (APM)
Server health monitoring
Infrastructure monitoring for cloud environments
IT operations management (ITOM)
Security and compliance monitoring
Experience the power of Lert!
Unlock new possibilities for your business with Lert.
Related Blogs
Top 10 Overlooked User Experience Best Practices in Design
User experience (UX) design is an important aspect of creating successful digital products. However, despite its importance, some crucial UX best practices are often overlooked in the design process. In this blog post, we will discuss ten often-overlooked UX best...
Why OTPs shouldn’t be part of a passwordless strategy
One-time passwords (OTPs) are a common way to add an extra layer of security to an authentication process, but they can still be vulnerable to attacks and are not recommended as a sole means of authentication in a passwordless strategy. OTPs rely on the assumption...
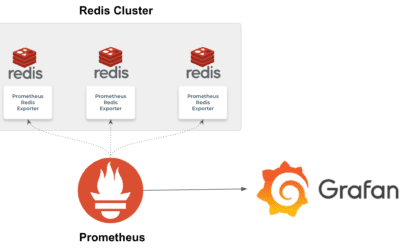
Monitoring REDIS using Prometheus and Grafana
Redis is a popular open-source in-memory database which can also be used as a message broker. It can be scaled (lineraly) to handle large volumes and throughputs of an order of 50 million ops per second. Redis can be considered as a key-value store, but the uniqueness...